As an iPhone photographer, you’re likely no stranger to the challenges of capturing stunning images with a camera that’s stuck in your pocket. But fear not! With these 7 iPhone photography hacks, you’ll be able to take your photos to the next level and impress even the most discerning eye.
- Use Reflections to Add Depth
One of the most effective ways to add depth and interest to your iPhone photos is by incorporating reflections. Whether it’s a mirror, window, or puddle, use the reflective surface to create a sense of symmetry and dimensionality in your shot.
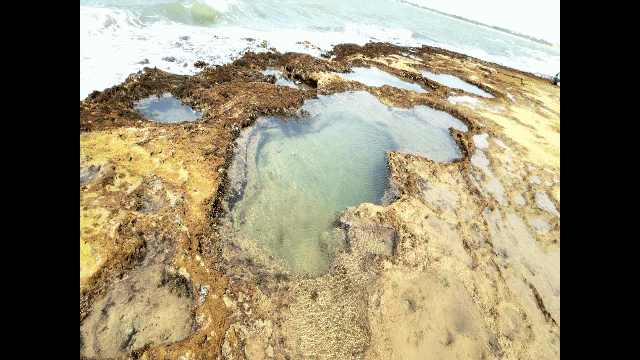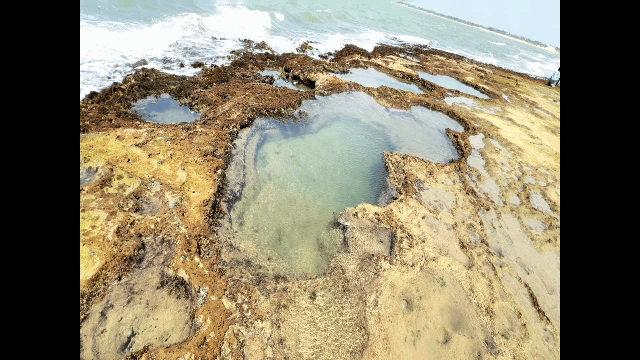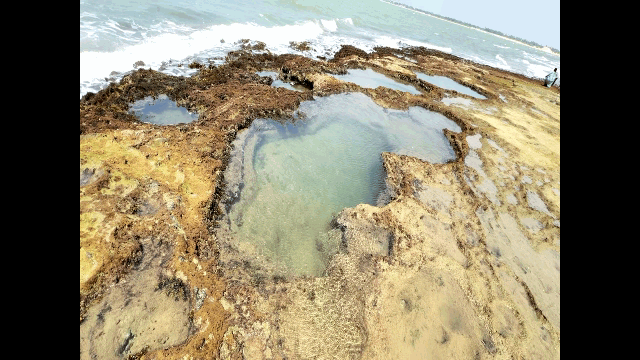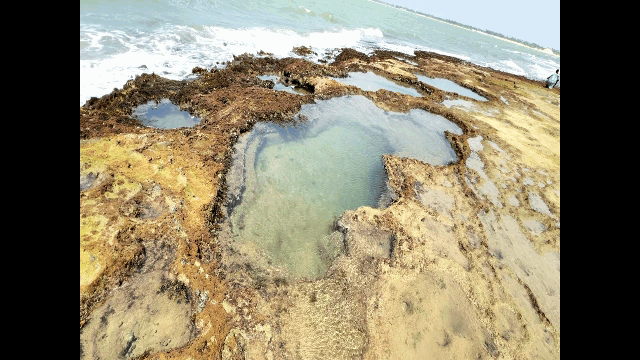
To do this, simply position yourself at an angle to the reflection and adjust your composition accordingly. You can also experiment with different angles and perspectives to create more dynamic shots.
2. Play with Perspective
Perspective is everything when it comes to iPhone photography. By experimenting with different vantage points and compositions, you can add depth, interest, and even a sense of storytelling to your photos.
Try shooting from low or high angles, using staircases, archways, or other structures to create unique perspectives, or experimenting with forced perspective (where two objects appear to be the same size) for added visual interest.
Churches are ideal for architectural photography as the tall spires with intricate stone work contrast with the brick work of the lateral walls against the tapestry of the blue skies. Architectural photographers love capturing the unique details and textures that make each church unique, from the ornate carvings to the intricate patterns and designs. The play of light on the stone and brickwork can create stunning effects, highlighting the craftsmanship and beauty of these historic structures.
The adjacent photo sums up this.

3. Use Lighting to Create Mood
Lighting is one of the most powerful tools in your iPhone photography arsenal. By using natural light, artificial light, or a combination of both, you can create mood, atmosphere, and even tell stories through your photos.
Experiment with different lighting conditions, such as golden hour, blue hour, or even nighttime shots lit by streetlights or neon signs. You can also use the built-in iPhone flashlight to add some creative flair to your low-light shots.
4. Create Compositions That Tell a Story
One of the most effective ways to make your iPhone photos stand out is by creating compositions that tell a story. Whether it’s capturing a moment, documenting a scene, or simply showcasing an interesting subject, use your composition to draw the viewer in and keep them engaged.

Try using leading lines, framing devices, or even simple gestures to create visual interest and guide the viewer’s eye through your photo. You can also experiment with different angles, perspectives, and vantage points to add more depth and storytelling potential to your shots.
5. Experiment with Motion Blur
Motion blur is a powerful technique that can add energy, movement, and dynamism to your iPhone photos. By panning or following your subject as it moves, you can create beautiful blurs that convey the sense of motion and action.
Try capturing speeding cars, running animals, or even blurred waterfalls for added visual interest. You can also experiment with slower speeds, such as blurred people walking or trees swaying in the wind, to add more texture and depth to your shots.
6. Use Your iPhone’s Built-In Features
One of the best things about iPhone photography is the sheer range of built-in features at your disposal. From the HDR mode to the built-in filters and editing tools, there are plenty of ways to enhance and transform your photos without needing any additional apps or equipment.
The iPhone camera offers various modes to help you capture great photos, including Burst Mode for fast-moving subjects, Long Exposure for motion blur effects, Portrait Mode for blurred backgrounds, and HDR (High Dynamic Range) for better color and detail. You can also customize photographic styles with tone and warmth sliders. Convenience features include quick access to the camera, using volume buttons as a shutter, and a grid for composition. For more control, you can lock focus and exposure settings or make manual adjustments. Video features include Cinematic Mode on iPhone 13 and newer, which automates focus transitions, and Optical Image Stabilization to reduce shakes during recording.

Experiment with different modes, such as Burst Mode for capturing fast-moving subjects or Time-Lapse for creating stunning sequences, and don’t be afraid to get creative with the editing tools to add more flair and personality to your shots.
7. Shoot in RAW
Finally, one of the most effective ways to take your iPhone photography to the next level is by shooting in RAW format. This allows you to capture images with greater dynamic range, color accuracy, and detail than JPEGs, making it ideal for landscapes, portraits, or any shot where you want maximum flexibility when editing.
A RAW image format is an uncompressed and unprocessed file captured directly from a camera’s sensor. It contains all the image data without compression or adjustments like white balance, exposure, or sharpness. Usually professional cameras would offer the option to save it RAW format. Before we set up the iPhone to save in RAW format, we will see what that means:

Key Features of RAW Format
Uncompressed Data – Retains full sensor details without loss.
Higher Dynamic Range – Preserves shadows and highlights better.
Editable Without Quality Loss – Allows adjustments without degrading image quality.
Larger File Size – RAW files are much bigger than JPEGs due to the lack of compression.
To shoot in RAW on your iPhone (Pro models only), simply open the Camera app, select “ProRAW” as your file format, and start snapping. The file size of a ProRAW image at 12MP resolution is approximately 25 MB, and the file size at 48MP is approximately 75 MB.If you have iPhone 11 or later, you can use Camera + app to select this RAW option.
You can then edit your photos using third-party apps like Adobe Lightroom or Capture One, which offer more advanced RAW processing capabilities than the built-in Photos app.
There you have it – 7 iPhone photography hacks to help you take your photos to the next level. Whether you’re a seasoned pro or just starting out with mobile photography, these tips and tricks are sure to help you capture stunning images that will leave everyone wanting more. So go ahead, get creative, and see where your iPhone photography journey takes you!